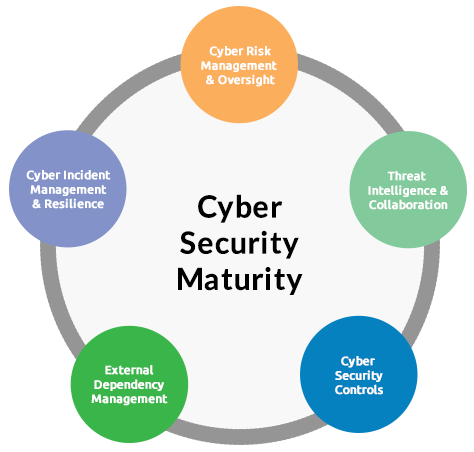
Information System Maturity Assessment
To ensure security, it is important to build-in security in both the planning and the design phases and adapt a security architecture which makes sure that regular and security related tasks, are deployed correctly. Security requirements must be linked to the business goals. We identified four domains that affect security at an organization namely, organization governance, organizational culture, the architecture of the systems, and service management. In order to identify and explore the strength and weaknesses of particular organization's security, a wide range model has been developed. This model is proposed as an information security maturity model (ISMM) and it is intended as a tool to evaluate the ability of organizations to meet the objectives of security.
Below are the level of compliance which determine Information security level in any organisation.
1. None Compliance
This state is characterizing by no existence of policies and procedures to secure the business. Management doesn’t consider investing in security related systems necessary for overall business strategies.
2. Initial compliance:
This state is starting point of any organization. As long as an organization is conscious about the threats that their information systems face then that organization is considered at initial stage of ISMM. This stage is characterizing by being chaotic, inconsistence, ad hoc, and in response to attacks and possibly because of losing resources due to an attack.
3. Basic compliance:
This state is starting point of any organization that wants to protect its investment and ensure continuity. Application and network security is implemented but changes are not centrally managed and ad hoc security requested are common. IT security procedure is informally defined and some risk assessments are taking place. In addition, responsibilities for IT security have been assigned but enforcement is inconsistence. Some intrusion and detection testing can also be performed.
4. Acceptable compliance:
This state is characterized by central management of all security related issues and policies. Users are trusted but their interactions with the systems are viewed as vulnerability. No ad hoc changes and central configuration models, from which all configurations are derived, are implemented. Security policies and procedures are now in place together with adequate delivery mechanisms to aid awareness and compliance. Access controls are mandatory and are closely monitored. Security measures are introduced on a cost/benefit basis and ownership concept is in place.
5. Full compliance:
This state is characterized by having control over the security needs of the organization, monitoring the systems, being aware of threats and benchmarking by comparing the organization itself to other similar organizations and to international standards. In addition, a comprehensive security function has been established that is both cost effective and efficient which delivers high quality implementation. This comprehensive plan has formal policies and procedures in place to prevent, detect, and correct any security related issues. Also, corporate governance is aligned with the security needs of an organization. Corporate governance has policies for internal auditing which is independent and objective activity designed to add value and improve the security of the organization. The result of any audit activity is published and actions are implemented.
Our Approach
Our approach at ForceOne securities is to fully understand customer business , their current IT system along with criticality on the business operation. We perform gap assessment of current IT maturity level and the requirement of business, along with future IT trend and technologies. Our solution consists not only vanilla deployment of standard ISMM, but integrate with business and create synergy of IT and business to help in focusing on the core area.
